The DevOps space is in a constant state of change and innovation. One area that has seen significant growth in recent years is the use of monolithic repos, or monorepos. A monorepo allows you to store many codebases in a single repository, whereas multi-repos are many repositories that are all linked to each other. Several large technology companies, including Facebook, Google, and Uber have incorporated monorepos as a basic component of their architecture.
The use of monorepos can help companies save time on management, testing, and debugging. Many of these benefits come from having all the code in a centralized, easily accessible place. This makes it easier to view and manage dependencies and interactions amongst the packages. There are also fewer dependencies between projects for developers to worry about when deploying new features or updates. Monorepos have been gaining popularity because they enable faster iterations for product development without worrying about breaking other parts of the project, while allowing changes to be made quickly, with less risk for merge conflicts.
In practice, working in a monorepo implies that one is always working out of the HEAD (also known as the master, main, or trunk branches) instead of the development branch, which is typical in Git workflows.


source: fpy.cz
Instead of working on a branch that is pulled from HEAD, which can become quickly outdated, everybody works on HEAD (in the above diagram, master). With multiple repos, libraries that are pinned to specific versions are scattered about. This makes it difficult to identify callers and update dependencies across projects. With monorepos, all libraries and their dependencies are accessible on HEAD. This makes identifying all current callers simple, as users are aware of which clients need to be updated automatically.
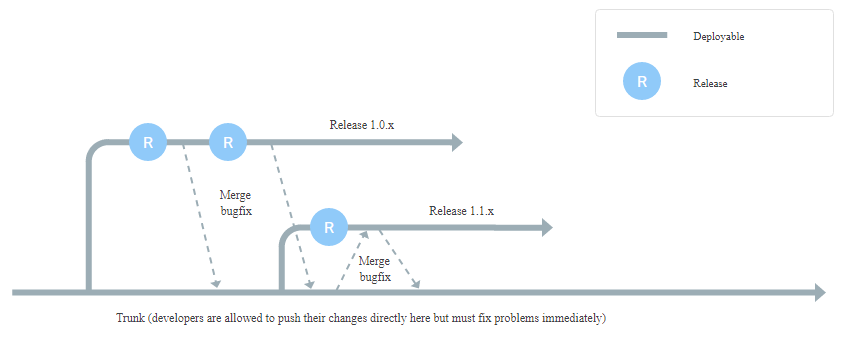

Release branches are published off of HEAD, like taking an exit off of the development highway. Source: cloud.google.com/architecture/devops
Adopting a monorepo strategy also enables the ability to track changes and clean up one’s dependency management throughout a codebase. Having all the code in one place makes it easier to find and fix errors, as well as make changes quickly without worrying about breaking other parts of the project. Additionally, using a monorepo allows developers to more easily share code between projects, which can save time and development resources.
Despite all of their benefits, monorepos introduce new security risks to source code management and build processes. The following section covers a few of the potential security risks and mitigation techniques.
Access Control
Risk
One of the key considerations for companies when implementing a monorepo is access control. When all of the code is stored in a single repository, it can be difficult to track who has access to which files and folders. It's also more difficult to revoke access if someone no longer needs access to certain files in different parts of the monorepo at scale.
Mitigation
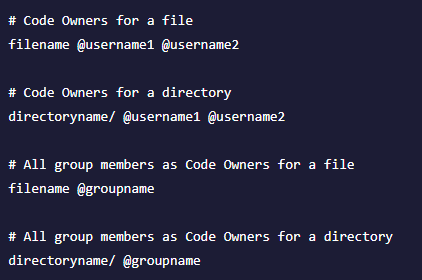
Enterprises typically handle their access controls and privileges at the repo level in the multi-repo world, but they must be scoped at the file or folder levels in the monorepo world. The Git codeowners feature allows this with GitLab monorepos. Individuals or teams that are in charge of files or directories in a repository are referred to as code owners. When someone opens a pull request to modify code, the code owners are immediately requested to review it. Managing the lifecycles of code owner permissions and wiring them back to a central entitlements system is not simple, but is critical to establishing a procedure for handling code owners’ entitlements.

High Availability and Performance
Risk
When enterprises decide to use a monorepo, they must deal with performance and availability risks. As the codebase expands, it may become more difficult to maintain and scale, especially with hosted editions of version control needing to handle thousands of transactions (code changes) per hour. Additionally, as the repository becomes larger, it can take longer for developers to clone it and build it. In order to mitigate these risks, companies need to have a clear plan for scaling their monorepo. This plan should include measures for optimizing performance and ensuring availability.
Mitigation
Git provides many features that enhance developer productivity, including shallow clones, sparse checkout and LFS. Another alternative is to not use decentralized and distributed version controls, such as Git, and to instead keep your local codebase in sync all the time by using centralized version control tools such as Perforce to improve push/pull efficiency.
Breaking Changes
Risk
One of the key advantages of utilizing a monorepo is that it reduces development time by allowing for more code sharing between projects. This standardization allows for easy comprehension of another team's codebase, making it easier to address issues or bugs in random projects that impact one’s build.
However, this also introduces a new risk of breaking changes, such as massive refactoring, restructuring the code, or code cleanups. When code is shared between projects, it is possible for changes made in one project to break the code in another project, as the code is interdependent in a monorepo. This can be especially risky if two projects used by different teams are in different stages of development. To mitigate this risk, companies need to have a clear plan for managing breaking changes. This plan should include measures for identifying and tracking breaking changes, testing breaking changes before they are merged into the main codebase and rolling back breaking changes if they cause problems.
Mitigation
This is where build systems such as Bazel or Buck, which understand the linkages between code commits, shine. Bazel recognizes the dependencies involved with large changes and builds a dependency graph to better assess their effect. Only the sections of the source code that have changed since the prior build may be recompiled with this approach. Additionally, Bazel has a built-in caching mechanism that speeds up the build process, making it ideal for governing the build hygiene for large codebases.


A sample dependency graph that Bazel has generated. Source: https://docs.bazel.build/versions/4.2.1/skylark/aspects.html
Supply Chain Protection
Risk
Supply chain attacks are a real and present danger to enterprise security, and monorepos might increase the risk of these types of attacks. Because all the code is housed in one place, it's easier for attackers to find and exploit vulnerabilities in the code.
Mitigation
This exemplifies the importance of running vulnerability scanning and composition analysis (which are common security practices to mitigate supply chain attacks) of software packages as a part of Git CI pipelines in monorepos. However, many providers do not include vulnerability scanning as part of their Bazel build CI pipelines. This is due to the fact that Bazel build does not contain dependency manifest files or lock files, as package managers such as npm do. Instead, the configuration is maintained in BUILD files written in Starlark, a Python3-based domain-specific language. This makes it difficult for modern-day vulnerability scanners to find out which packages (and their transitive dependencies) are required by the project out of the box.
This risk can be reduced by pointing the Bazel build to internal software artifact repositories and allowing only scanned libraries to be ingested. If keeping up with such an up-to-date software asset inventory is difficult, it's a good idea to build a wrapper or an API around the software composition and vulnerability analysis platforms to process the Bazel dependency graph as a payload and evaluate the provenance of each library and all transitive dependencies linked to the project. Such provenance may be established by SLSA Software Attestations and in-toto attestation framework.


A sample flattened list of the dependency graph generated by Bazel. Source: https://docs.bazel.build/versions/main/query-how-to.html
Cache Poisoning
Risk
In the monorepo world, remote build caches are typically used by developers and CI systems to share build outputs. If your build is reproducible, the outputs from one machine can be safely reused on another machine, which can make builds significantly faster. However, they can also be susceptible to attack. In a monorepo, an attacker could poison the build cache by inserting a malicious build that would be recompiled every time, which might result in a supply chain compromise.
Mitigation
To minimize this threat, it is critical to protect the build caches for each project. Using authentication and authorization procedures to ensure that only authorized people can access the build cache is essential. It is also prudent to monitor the build cache for any unexpected changes that indicate an attack.
Closing Thoughts
Overall, there are several advantages to working with a monorepo. However, just as with any large codebase, there are specific procedures and tooling that must be in place to keep it secure. You may reap the benefits while still keeping your codebase secure by understanding the risks involved with monorepos and implementing necessary controls to mitigate them.
Want to learn more about exciting engineering opportunities at Goldman Sachs? Explore our careers page.
See https://www.gs.com/disclaimer/global_email for important risk disclosures, conflicts of interest, and other terms and conditions relating to this blog and your reliance on information contained in it.
Solutions
Curated Data Security MasterData AnalyticsPlotTool ProPortfolio AnalyticsGS QuantTransaction BankingGS DAP®Liquidity Investing¹ Real-time data can be impacted by planned system maintenance, connectivity or availability issues stemming from related third-party service providers, or other intermittent or unplanned technology issues.
Transaction Banking services are offered by Goldman Sachs Bank USA ("GS Bank") and its affiliates. GS Bank is a New York State chartered bank, a member of the Federal Reserve System and a Member FDIC. For additional information, please see Bank Regulatory Information.
² Source: Goldman Sachs Asset Management, as of March 31, 2025.
Mosaic is a service mark of Goldman Sachs & Co. LLC. This service is made available in the United States by Goldman Sachs & Co. LLC and outside of the United States by Goldman Sachs International, or its local affiliates in accordance with applicable law and regulations. Goldman Sachs International and Goldman Sachs & Co. LLC are the distributors of the Goldman Sachs Funds. Depending upon the jurisdiction in which you are located, transactions in non-Goldman Sachs money market funds are affected by either Goldman Sachs & Co. LLC, a member of FINRA, SIPC and NYSE, or Goldman Sachs International. For additional information contact your Goldman Sachs representative. Goldman Sachs & Co. LLC, Goldman Sachs International, Goldman Sachs Liquidity Solutions, Goldman Sachs Asset Management, L.P., and the Goldman Sachs funds available through Goldman Sachs Liquidity Solutions and other affiliated entities, are under the common control of the Goldman Sachs Group, Inc.
Goldman Sachs & Co. LLC is a registered U.S. broker-dealer and futures commission merchant, and is subject to regulatory capital requirements including those imposed by the SEC, the U.S. Commodity Futures Trading Commission (CFTC), the Chicago Mercantile Exchange, the Financial Industry Regulatory Authority, Inc. and the National Futures Association.
FOR INSTITUTIONAL USE ONLY - NOT FOR USE AND/OR DISTRIBUTION TO RETAIL AND THE GENERAL PUBLIC.
This material is for informational purposes only. It is not an offer or solicitation to buy or sell any securities.
THIS MATERIAL DOES NOT CONSTITUTE AN OFFER OR SOLICITATION IN ANY JURISDICTION WHERE OR TO ANY PERSON TO WHOM IT WOULD BE UNAUTHORIZED OR UNLAWFUL TO DO SO. Prospective investors should inform themselves as to any applicable legal requirements and taxation and exchange control regulations in the countries of their citizenship, residence or domicile which might be relevant. This material is provided for informational purposes only and should not be construed as investment advice or an offer or solicitation to buy or sell securities. This material is not intended to be used as a general guide to investing, or as a source of any specific investment recommendations, and makes no implied or express recommendations concerning the manner in which any client's account should or would be handled, as appropriate investment strategies depend upon the client's investment objectives.
United Kingdom: In the United Kingdom, this material is a financial promotion and has been approved by Goldman Sachs Asset Management International, which is authorized and regulated in the United Kingdom by the Financial Conduct Authority.
European Economic Area (EEA): This marketing communication is disseminated by Goldman Sachs Asset Management B.V., including through its branches ("GSAM BV"). GSAM BV is authorised and regulated by the Dutch Authority for the Financial Markets (Autoriteit Financiële Markten, Vijzelgracht 50, 1017 HS Amsterdam, The Netherlands) as an alternative investment fund manager ("AIFM") as well as a manager of undertakings for collective investment in transferable securities ("UCITS"). Under its licence as an AIFM, the Manager is authorized to provide the investment services of (i) reception and transmission of orders in financial instruments; (ii) portfolio management; and (iii) investment advice. Under its licence as a manager of UCITS, the Manager is authorized to provide the investment services of (i) portfolio management; and (ii) investment advice.
Information about investor rights and collective redress mechanisms are available on www.gsam.com/responsible-investing (section Policies & Governance). Capital is at risk. Any claims arising out of or in connection with the terms and conditions of this disclaimer are governed by Dutch law.
To the extent it relates to custody activities, this financial promotion is disseminated by Goldman Sachs Bank Europe SE ("GSBE"), including through its authorised branches. GSBE is a credit institution incorporated in Germany and, within the Single Supervisory Mechanism established between those Member States of the European Union whose official currency is the Euro, subject to direct prudential supervision by the European Central Bank (Sonnemannstrasse 20, 60314 Frankfurt am Main, Germany) and in other respects supervised by German Federal Financial Supervisory Authority (Bundesanstalt für Finanzdienstleistungsaufsicht, BaFin) (Graurheindorfer Straße 108, 53117 Bonn, Germany; website: www.bafin.de) and Deutsche Bundesbank (Hauptverwaltung Frankfurt, Taunusanlage 5, 60329 Frankfurt am Main, Germany).
Switzerland: For Qualified Investor use only - Not for distribution to general public. This is marketing material. This document is provided to you by Goldman Sachs Bank AG, Zürich. Any future contractual relationships will be entered into with affiliates of Goldman Sachs Bank AG, which are domiciled outside of Switzerland. We would like to remind you that foreign (Non-Swiss) legal and regulatory systems may not provide the same level of protection in relation to client confidentiality and data protection as offered to you by Swiss law.
Asia excluding Japan: Please note that neither Goldman Sachs Asset Management (Hong Kong) Limited ("GSAMHK") or Goldman Sachs Asset Management (Singapore) Pte. Ltd. (Company Number: 201329851H ) ("GSAMS") nor any other entities involved in the Goldman Sachs Asset Management business that provide this material and information maintain any licenses, authorizations or registrations in Asia (other than Japan), except that it conducts businesses (subject to applicable local regulations) in and from the following jurisdictions: Hong Kong, Singapore, India and China. This material has been issued for use in or from Hong Kong by Goldman Sachs Asset Management (Hong Kong) Limited and in or from Singapore by Goldman Sachs Asset Management (Singapore) Pte. Ltd. (Company Number: 201329851H).
Australia: This material is distributed by Goldman Sachs Asset Management Australia Pty Ltd ABN 41 006 099 681, AFSL 228948 (‘GSAMA’) and is intended for viewing only by wholesale clients for the purposes of section 761G of the Corporations Act 2001 (Cth). This document may not be distributed to retail clients in Australia (as that term is defined in the Corporations Act 2001 (Cth)) or to the general public. This document may not be reproduced or distributed to any person without the prior consent of GSAMA. To the extent that this document contains any statement which may be considered to be financial product advice in Australia under the Corporations Act 2001 (Cth), that advice is intended to be given to the intended recipient of this document only, being a wholesale client for the purposes of the Corporations Act 2001 (Cth). Any advice provided in this document is provided by either of the following entities. They are exempt from the requirement to hold an Australian financial services licence under the Corporations Act of Australia and therefore do not hold any Australian Financial Services Licences, and are regulated under their respective laws applicable to their jurisdictions, which differ from Australian laws. Any financial services given to any person by these entities by distributing this document in Australia are provided to such persons pursuant to the respective ASIC Class Orders and ASIC Instrument mentioned below.
- Goldman Sachs Asset Management, LP (GSAMLP), Goldman Sachs & Co. LLC (GSCo), pursuant ASIC Class Order 03/1100; regulated by the US Securities and Exchange Commission under US laws.
- Goldman Sachs Asset Management International (GSAMI), Goldman Sachs International (GSI), pursuant to ASIC Class Order 03/1099; regulated by the Financial Conduct Authority; GSI is also authorized by the Prudential Regulation Authority, and both entities are under UK laws.
- Goldman Sachs Asset Management (Singapore) Pte. Ltd. (GSAMS), pursuant to ASIC Class Order 03/1102; regulated by the Monetary Authority of Singapore under Singaporean laws
- Goldman Sachs Asset Management (Hong Kong) Limited (GSAMHK), pursuant to ASIC Class Order 03/1103 and Goldman Sachs (Asia) LLC (GSALLC), pursuant to ASIC Instrument 04/0250; regulated by the Securities and Futures Commission of Hong Kong under Hong Kong laws
No offer to acquire any interest in a fund or a financial product is being made to you in this document. If the interests or financial products do become available in the future, the offer may be arranged by GSAMA in accordance with section 911A(2)(b) of the Corporations Act. GSAMA holds Australian Financial Services Licence No. 228948. Any offer will only be made in circumstances where disclosure is not required under Part 6D.2 of the Corporations Act or a product disclosure statement is not required to be given under Part 7.9 of the Corporations Act (as relevant).
FOR DISTRIBUTION ONLY TO FINANCIAL INSTITUTIONS, FINANCIAL SERVICES LICENSEES AND THEIR ADVISERS. NOT FOR VIEWING BY RETAIL CLIENTS OR MEMBERS OF THE GENERAL PUBLIC
Canada: This presentation has been communicated in Canada by GSAM LP, which is registered as a portfolio manager under securities legislation in all provinces of Canada and as a commodity trading manager under the commodity futures legislation of Ontario and as a derivatives adviser under the derivatives legislation of Quebec. GSAM LP is not registered to provide investment advisory or portfolio management services in respect of exchange-traded futures or options contracts in Manitoba and is not offering to provide such investment advisory or portfolio management services in Manitoba by delivery of this material.
Japan: This material has been issued or approved in Japan for the use of professional investors defined in Article 2 paragraph (31) of the Financial Instruments and Exchange Law ("FIEL"). Also, any description regarding investment strategies on or funds as collective investment scheme under Article 2 paragraph (2) item 5 or item 6 of FIEL has been approved only for Qualified Institutional Investors defined in Article 10 of Cabinet Office Ordinance of Definitions under Article 2 of FIEL.
Interest Rate Benchmark Transition Risks: This transaction may require payments or calculations to be made by reference to a benchmark rate ("Benchmark"), which will likely soon stop being published and be replaced by an alternative rate, or will be subject to substantial reform. These changes could have unpredictable and material consequences to the value, price, cost and/or performance of this transaction in the future and create material economic mismatches if you are using this transaction for hedging or similar purposes. Goldman Sachs may also have rights to exercise discretion to determine a replacement rate for the Benchmark for this transaction, including any price or other adjustments to account for differences between the replacement rate and the Benchmark, and the replacement rate and any adjustments we select may be inconsistent with, or contrary to, your interests or positions. Other material risks related to Benchmark reform can be found at https://www.gs.com/interest-rate-benchmark-transition-notice. Goldman Sachs cannot provide any assurances as to the materialization, consequences, or likely costs or expenses associated with any of the changes or risks arising from Benchmark reform, though they may be material. You are encouraged to seek independent legal, financial, tax, accounting, regulatory, or other appropriate advice on how changes to the Benchmark could impact this transaction.
Confidentiality: No part of this material may, without GSAM's prior written consent, be (i) copied, photocopied or duplicated in any form, by any means, or (ii) distributed to any person that is not an employee, officer, director, or authorized agent of the recipient.
GSAM Services Private Limited (formerly Goldman Sachs Asset Management (India) Private Limited) acts as the Investment Advisor, providing non-binding non-discretionary investment advice to dedicated offshore mandates, involving Indian and overseas securities, managed by GSAM entities based outside India. Members of the India team do not participate in the investment decision making process.