Background
Entitlements is a paradigm that fundamentally tries to answer the question “Given that we already know who a particular user is, what is the user entitled to do in an application?”. Questions we typically ask are:
- “What is Jane allowed to do in the application?"
- "Can John view the sales report or only specific data in a sales report?”
- "Can Jose call an API?”
- “Who is allowed to view this proprietary data?”
As Goldman Sachs continues to expand its footprint on the public cloud, it is imperative that the firm protects its data. This commitment has led to the genesis of an Open standards-based Cloud Entitlements Service (OCES). It offers a firmwide policy-based, attribute-driven entitlements platform. In this post, we will share approaches and best practices that can be applied to similar entitlements challenges at scale in financial services and other domains by leveraging serverless compute services and managed streaming products offered by Amazon Web Services (AWS), coupled with Open Policy Agent.
Prior to the introduction of Cloud Entitlements Service, there were several challenges including:
- Management of entitlement logic in code instead of a centralized entitlements engine
- Absence of a singular platform to review entitlements decisions and access provisioning audits
- Increase in operational complexity
- Taking on runtime dependencies to on-premise systems
The firm required a platform whereby any business unit could enforce entitlements on public cloud providers with the same ease that they would have on-premises. Given the time and sensitivity of activities the firm supports, it was paramount that any solution be available on a 24/7 basis with four 9s of availability. In a similar manner, it had to not only support monitoring and observability of the service and its infrastructure but also of the policy distribution and reference data events.
Solution
OCES provides a centralized policy engine hosted on the AWS platform. OCES is based on Open Policy Agent (OPA), which is an open source, general-purpose policy engine that provides a high-level declarative language and lets developers specify policy as code and use simple APIs to offload policy decision-making from application code. OCES provides a policy-as-code lifecycle for simple policy authoring, and supports monitoring and distribution of policy and reference data events at scale to OPA policy engines. OCES is multi-tenanted offering dedicated OPA tenants for various business areas in the firm. They get consistent service level guarantees since this service utilizes managed streaming, elastic scaling, and operational efficiencies of serverless compute infrastructure in the cloud. Further, OPA has gained wide acceptance across industries as a cloud-native, open source, general-purpose policy engine that unifies policy enforcement.
The overall architecture of OCES can be seen in the illustration below. The next section describes various components in detail.
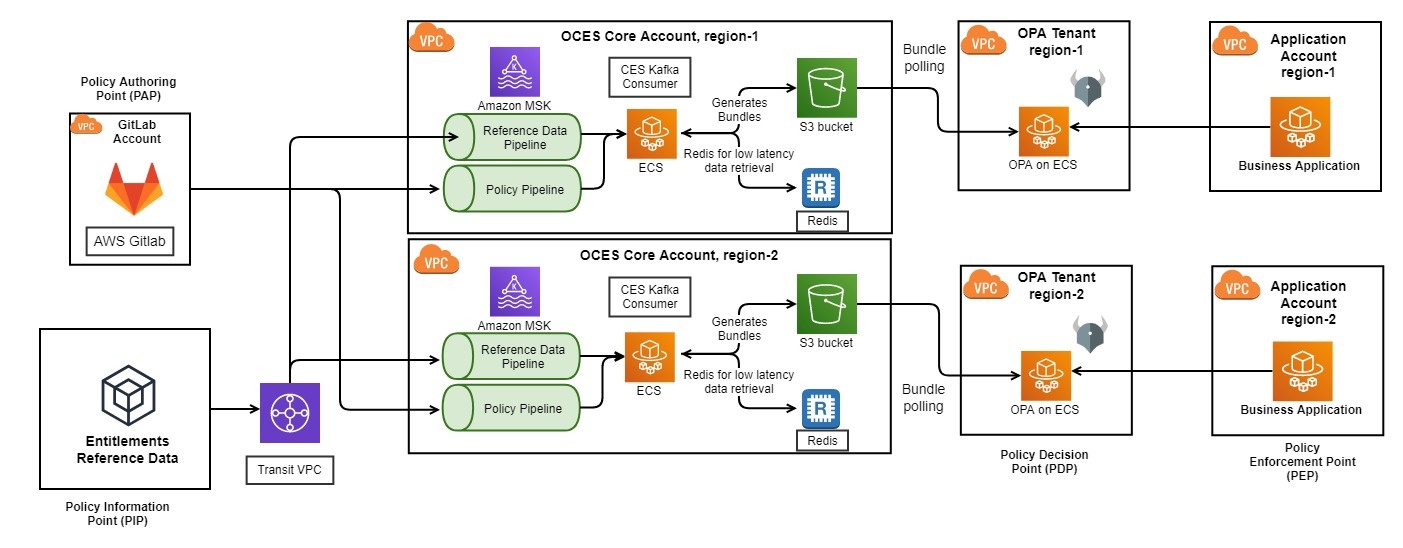

Components
The components of OCES can be viewed in reference to a Standards Control Architecture.
At a high-level they are:
Policy Enforcement Point (PEP)
The PEP is where entitlements are actually enforced. The supported enforcement points include:
- An application or an API
- An API Gateway
Policy Decision Point (PDP)
OPA clusters provide a highly available, reliable, and scalable PDP. Policies authored by application owners and associated reference data for a policy are evaluated by OPA to provide decisions that can be enforced by applications and APIs that integrate with OPA.
Policy Authoring Point (PAP)
OPA policies are authored in a declarative language called REGO which was inspired by Datalog. Within the OCES ecosystem, application owners author policies in GitLab which are subsequently pushed to the OPA PDPs using the GitLab CI/CD pipeline. Policies are subject to standard SDLC practices such as approval, testing, and baking in lower environments prior to being published to Production.
Policy Information Point (PIP)
Policies allow application owners to prescribe rules on who can or cannot use their systems. However, policies by themselves comprise of 50% of the input. Reference data forms a critical component of policy evaluation and is the remaining 50% of the input. Examples of reference data include 1) role memberships, 2) attribute assignments on a subject accessing a privileged resource, 3) metadata about resources being accessed, etc.
Diverse and well-governed reference data can enable policy authors to author powerful policies, thereby empowering them to enforce fine grained entitlements. OCES integrates with several standard and governed reference data sources in Goldman Sachs with the ability to further extend these sources.
AWS Resources
Apache Kafka on Amazon MSK, Schema Registry
The first challenge we faced was making entitlements related reference data available on AWS for consumption. The solution needed to meet the following criteria; (i) reflect updates to the data on a near real-time basis, (ii) be easily accessible and given the sensitivity of this use case, (iii) be reliable and consistent. Given those requirements, we selected Amazon MSK.
Apache Kafka is an open source, event based, stream processing software with high-throughput, low latency data pipelines, streaming analytics, and out-of-the-box data integrations. Apache Kafka offers the necessary mission critical stability, ensuring zero message loss, guaranteed ordering, permanent and durable data storage, a great degree of scalability, and easy methods of interaction through client libraries and interfaces. However, an improper setup can detract from the benefits of an Apache Kafka deployment. Amazon MSK alleviates this by abstracting away the nuances of managing an Apache Kafka infrastructure.
Apache Kafka topics are separated by business unit to ensure business data separation. Two topics are maintained per business unit; one for entitlement policy updates and another for reference data updates. Avro Schemas and a schema registry are used to ensure messages adhered to a specified contract when they were being published to the Apache Kafka topics.
Open Policy Agent on Amazon ECS
OPA, is an open source entitlements engine that can enforce any business entitlements policy whether it is role-based or attribute-based. Policies are written in REGO which is a high-level declarative language and allows policies to be written as code and uses simple APIs to delegate complex policy decision-making away from application code. OCES leverages OPA as it was already a proven platform demonstrating a robust support for flexible policy authoring, efficient request evaluation, and meeting the firm's entitlement requirements.
OCES has been designed as a multi-tenanted platform offering each business unit their own dedicated OPA tenant, which is well suited to OPA's lightweight nature. This flexibility allows business units across Goldman Sachs to use the platform to its fullest extent without interfering with each other. This topology was also suitable from the perspective of data separation and for limiting the impact across the firm should any engine outages occur. OCES has also been developed as a multi-regional service to ensure the platform would be resilient to any regional outages. OPA has been deployed on an Amazon ECS Fargate cluster as it greatly reduces the overhead of managing an already complex platform, especially when deploying several instances and across multiple regions.
Redis on Amazon ElastiCache
OPA provides two mechanisms for supplying an engine with relevant data and policies required for making entitlement decisions. (i) a push-paradigm where the OPA engine has to be loaded via a REST interface that the engine exposes out-of-the-box, and (ii) a pull-paradigm where the engine is configured to periodically download a bundle (a tarball comprising of the necessary data and policy files), and activates it. Given that these approaches cannot be used in conjunction with each other, we chose the pull-based approach as it was more suitable for OCES' requirements. This bundle is periodically recreated to include any new reference data or policy changes that were observed since the previous bundle generation.
Performant reads and writes were essential for the rapid generation of these bundles. This becomes an important requirement especially where there are bulk entitlement events (such as onboarding a new client) that could generate several hundred thousand events. Redis, an open source, in-memory, key-value store offered the performance and high availability necessary to fit into the OCES infrastructure. Amazon ElastiCache facilitated rapidly standing up a Redis cluster that met the requirements. As new events are recorded on the Apache Kafka topics, they are written into Redis ensuring data isolation is maintained by partitioning the data in the cluster based on the topic where the data originated from. A separate process runs periodically, based on a schedule, and reads in all the data in a specific partition and generates a corresponding data file that will be used by the engine. The generated data file is bundled into the tarball with the most recent version of the policy and is written to Amazon S3 where the engine will download the bundle from.
Lessons Learned
1. Outages are a reality - building for resiliency is a necessity
Entitlements are a fundamental prerequisite for accessing any application. OCES provides a critical service for applications on the cloud and hence availability and resiliency are non-negotiable. As we started designing the solution and started thinking about Ops and Observability, building for resiliency through a multi-region topology became a core tenet.
2. The nature of a domain and its specific requirements constrains flexibility offered by technology
A very important lesson that we learned while designing OCES is that nature of the domain we operate in enforces constraints that are otherwise not applicable when using a framework or technology. As an example, events that occur on any entitlement reference data must be strictly ordered when published to AWS. This ordering is important to ensure accurate entitlement decisions. This serial ordering limited the optimizations that we could have performed in the Kafka publication.
3. When presented with multiple conflicting options, avoid choices that lead to one-way doors
When thinking about scalability and maintenance of the platform, we were presented with options such as running OPA as tenants that applications could connect to vs. running OPA agents as sidecars for every application. There are pros and cons of each approach. The obvious downside of the sidecar approach is that the number of agents can grow unchecked, thereby leading to considerable cost and control implications. However, with a centralized OPA tenant cluster model, there may be latency implications that might impact performance for certain applications. A lesson we learned when brainstorming these options is that while we build by making one design choice, it should not close the door of using a secondary design choice when there is a legitimate business need. Hence, while OCES offers centralized OPA tenants for businesses, the option to deploy sidecars is open and available.
4. Business separation is highly valued and is often a fundamental requirement
One of the core tenets for launching OCES was offering a multi-tenanted environment where we could provide business data separation and isolation. This model provides dedicated OPA tenants for lines of businesses in the firm. Multi-tenancy offers the flexibility to load only relevant policies and reference data for a tenant. We learned that there is a lot of value in this approach because we can shield each tenant from the usage patterns and load of other tenants.
Next Steps
The launch of OCES is just the beginning of a larger journey towards enabling entitlements management on a cloud environment operated by a firm such as Goldman Sachs. We are now focused on extending the initial offering of OCES to allow multiple businesses in the firm to model comprehensive business policies on the cloud. We are working towards features that would accelerate adoption across various businesses.
Conclusion
In this blog, we discussed how we developed an entitlements platform for Goldman Sachs’ cloud-native applications. We hope this post provides insight into how a variety of AWS services can be utilized in conjunction with OPA to orchestrate an entitlements platform that can be leveraged by a broad audience.
Want to learn more about exciting engineering opportunities at Goldman Sachs? Explore our careers page.
See https://www.gs.com/disclaimer/global_email for important risk disclosures, conflicts of interest, and other terms and conditions relating to this blog and your reliance on information contained in it.
Solutions
Curated Data Security MasterData AnalyticsPlotTool ProPortfolio AnalyticsGS QuantTransaction BankingGS DAP®Liquidity Investing¹ Real-time data can be impacted by planned system maintenance, connectivity or availability issues stemming from related third-party service providers, or other intermittent or unplanned technology issues.
Transaction Banking services are offered by Goldman Sachs Bank USA ("GS Bank") and its affiliates. GS Bank is a New York State chartered bank, a member of the Federal Reserve System and a Member FDIC. For additional information, please see Bank Regulatory Information.
² Source: Goldman Sachs Asset Management, as of March 31, 2025.
Mosaic is a service mark of Goldman Sachs & Co. LLC. This service is made available in the United States by Goldman Sachs & Co. LLC and outside of the United States by Goldman Sachs International, or its local affiliates in accordance with applicable law and regulations. Goldman Sachs International and Goldman Sachs & Co. LLC are the distributors of the Goldman Sachs Funds. Depending upon the jurisdiction in which you are located, transactions in non-Goldman Sachs money market funds are affected by either Goldman Sachs & Co. LLC, a member of FINRA, SIPC and NYSE, or Goldman Sachs International. For additional information contact your Goldman Sachs representative. Goldman Sachs & Co. LLC, Goldman Sachs International, Goldman Sachs Liquidity Solutions, Goldman Sachs Asset Management, L.P., and the Goldman Sachs funds available through Goldman Sachs Liquidity Solutions and other affiliated entities, are under the common control of the Goldman Sachs Group, Inc.
Goldman Sachs & Co. LLC is a registered U.S. broker-dealer and futures commission merchant, and is subject to regulatory capital requirements including those imposed by the SEC, the U.S. Commodity Futures Trading Commission (CFTC), the Chicago Mercantile Exchange, the Financial Industry Regulatory Authority, Inc. and the National Futures Association.
FOR INSTITUTIONAL USE ONLY - NOT FOR USE AND/OR DISTRIBUTION TO RETAIL AND THE GENERAL PUBLIC.
This material is for informational purposes only. It is not an offer or solicitation to buy or sell any securities.
THIS MATERIAL DOES NOT CONSTITUTE AN OFFER OR SOLICITATION IN ANY JURISDICTION WHERE OR TO ANY PERSON TO WHOM IT WOULD BE UNAUTHORIZED OR UNLAWFUL TO DO SO. Prospective investors should inform themselves as to any applicable legal requirements and taxation and exchange control regulations in the countries of their citizenship, residence or domicile which might be relevant. This material is provided for informational purposes only and should not be construed as investment advice or an offer or solicitation to buy or sell securities. This material is not intended to be used as a general guide to investing, or as a source of any specific investment recommendations, and makes no implied or express recommendations concerning the manner in which any client's account should or would be handled, as appropriate investment strategies depend upon the client's investment objectives.
United Kingdom: In the United Kingdom, this material is a financial promotion and has been approved by Goldman Sachs Asset Management International, which is authorized and regulated in the United Kingdom by the Financial Conduct Authority.
European Economic Area (EEA): This marketing communication is disseminated by Goldman Sachs Asset Management B.V., including through its branches ("GSAM BV"). GSAM BV is authorised and regulated by the Dutch Authority for the Financial Markets (Autoriteit Financiële Markten, Vijzelgracht 50, 1017 HS Amsterdam, The Netherlands) as an alternative investment fund manager ("AIFM") as well as a manager of undertakings for collective investment in transferable securities ("UCITS"). Under its licence as an AIFM, the Manager is authorized to provide the investment services of (i) reception and transmission of orders in financial instruments; (ii) portfolio management; and (iii) investment advice. Under its licence as a manager of UCITS, the Manager is authorized to provide the investment services of (i) portfolio management; and (ii) investment advice.
Information about investor rights and collective redress mechanisms are available on www.gsam.com/responsible-investing (section Policies & Governance). Capital is at risk. Any claims arising out of or in connection with the terms and conditions of this disclaimer are governed by Dutch law.
To the extent it relates to custody activities, this financial promotion is disseminated by Goldman Sachs Bank Europe SE ("GSBE"), including through its authorised branches. GSBE is a credit institution incorporated in Germany and, within the Single Supervisory Mechanism established between those Member States of the European Union whose official currency is the Euro, subject to direct prudential supervision by the European Central Bank (Sonnemannstrasse 20, 60314 Frankfurt am Main, Germany) and in other respects supervised by German Federal Financial Supervisory Authority (Bundesanstalt für Finanzdienstleistungsaufsicht, BaFin) (Graurheindorfer Straße 108, 53117 Bonn, Germany; website: www.bafin.de) and Deutsche Bundesbank (Hauptverwaltung Frankfurt, Taunusanlage 5, 60329 Frankfurt am Main, Germany).
Switzerland: For Qualified Investor use only - Not for distribution to general public. This is marketing material. This document is provided to you by Goldman Sachs Bank AG, Zürich. Any future contractual relationships will be entered into with affiliates of Goldman Sachs Bank AG, which are domiciled outside of Switzerland. We would like to remind you that foreign (Non-Swiss) legal and regulatory systems may not provide the same level of protection in relation to client confidentiality and data protection as offered to you by Swiss law.
Asia excluding Japan: Please note that neither Goldman Sachs Asset Management (Hong Kong) Limited ("GSAMHK") or Goldman Sachs Asset Management (Singapore) Pte. Ltd. (Company Number: 201329851H ) ("GSAMS") nor any other entities involved in the Goldman Sachs Asset Management business that provide this material and information maintain any licenses, authorizations or registrations in Asia (other than Japan), except that it conducts businesses (subject to applicable local regulations) in and from the following jurisdictions: Hong Kong, Singapore, India and China. This material has been issued for use in or from Hong Kong by Goldman Sachs Asset Management (Hong Kong) Limited and in or from Singapore by Goldman Sachs Asset Management (Singapore) Pte. Ltd. (Company Number: 201329851H).
Australia: This material is distributed by Goldman Sachs Asset Management Australia Pty Ltd ABN 41 006 099 681, AFSL 228948 (‘GSAMA’) and is intended for viewing only by wholesale clients for the purposes of section 761G of the Corporations Act 2001 (Cth). This document may not be distributed to retail clients in Australia (as that term is defined in the Corporations Act 2001 (Cth)) or to the general public. This document may not be reproduced or distributed to any person without the prior consent of GSAMA. To the extent that this document contains any statement which may be considered to be financial product advice in Australia under the Corporations Act 2001 (Cth), that advice is intended to be given to the intended recipient of this document only, being a wholesale client for the purposes of the Corporations Act 2001 (Cth). Any advice provided in this document is provided by either of the following entities. They are exempt from the requirement to hold an Australian financial services licence under the Corporations Act of Australia and therefore do not hold any Australian Financial Services Licences, and are regulated under their respective laws applicable to their jurisdictions, which differ from Australian laws. Any financial services given to any person by these entities by distributing this document in Australia are provided to such persons pursuant to the respective ASIC Class Orders and ASIC Instrument mentioned below.
- Goldman Sachs Asset Management, LP (GSAMLP), Goldman Sachs & Co. LLC (GSCo), pursuant ASIC Class Order 03/1100; regulated by the US Securities and Exchange Commission under US laws.
- Goldman Sachs Asset Management International (GSAMI), Goldman Sachs International (GSI), pursuant to ASIC Class Order 03/1099; regulated by the Financial Conduct Authority; GSI is also authorized by the Prudential Regulation Authority, and both entities are under UK laws.
- Goldman Sachs Asset Management (Singapore) Pte. Ltd. (GSAMS), pursuant to ASIC Class Order 03/1102; regulated by the Monetary Authority of Singapore under Singaporean laws
- Goldman Sachs Asset Management (Hong Kong) Limited (GSAMHK), pursuant to ASIC Class Order 03/1103 and Goldman Sachs (Asia) LLC (GSALLC), pursuant to ASIC Instrument 04/0250; regulated by the Securities and Futures Commission of Hong Kong under Hong Kong laws
No offer to acquire any interest in a fund or a financial product is being made to you in this document. If the interests or financial products do become available in the future, the offer may be arranged by GSAMA in accordance with section 911A(2)(b) of the Corporations Act. GSAMA holds Australian Financial Services Licence No. 228948. Any offer will only be made in circumstances where disclosure is not required under Part 6D.2 of the Corporations Act or a product disclosure statement is not required to be given under Part 7.9 of the Corporations Act (as relevant).
FOR DISTRIBUTION ONLY TO FINANCIAL INSTITUTIONS, FINANCIAL SERVICES LICENSEES AND THEIR ADVISERS. NOT FOR VIEWING BY RETAIL CLIENTS OR MEMBERS OF THE GENERAL PUBLIC
Canada: This presentation has been communicated in Canada by GSAM LP, which is registered as a portfolio manager under securities legislation in all provinces of Canada and as a commodity trading manager under the commodity futures legislation of Ontario and as a derivatives adviser under the derivatives legislation of Quebec. GSAM LP is not registered to provide investment advisory or portfolio management services in respect of exchange-traded futures or options contracts in Manitoba and is not offering to provide such investment advisory or portfolio management services in Manitoba by delivery of this material.
Japan: This material has been issued or approved in Japan for the use of professional investors defined in Article 2 paragraph (31) of the Financial Instruments and Exchange Law ("FIEL"). Also, any description regarding investment strategies on or funds as collective investment scheme under Article 2 paragraph (2) item 5 or item 6 of FIEL has been approved only for Qualified Institutional Investors defined in Article 10 of Cabinet Office Ordinance of Definitions under Article 2 of FIEL.
Interest Rate Benchmark Transition Risks: This transaction may require payments or calculations to be made by reference to a benchmark rate ("Benchmark"), which will likely soon stop being published and be replaced by an alternative rate, or will be subject to substantial reform. These changes could have unpredictable and material consequences to the value, price, cost and/or performance of this transaction in the future and create material economic mismatches if you are using this transaction for hedging or similar purposes. Goldman Sachs may also have rights to exercise discretion to determine a replacement rate for the Benchmark for this transaction, including any price or other adjustments to account for differences between the replacement rate and the Benchmark, and the replacement rate and any adjustments we select may be inconsistent with, or contrary to, your interests or positions. Other material risks related to Benchmark reform can be found at https://www.gs.com/interest-rate-benchmark-transition-notice. Goldman Sachs cannot provide any assurances as to the materialization, consequences, or likely costs or expenses associated with any of the changes or risks arising from Benchmark reform, though they may be material. You are encouraged to seek independent legal, financial, tax, accounting, regulatory, or other appropriate advice on how changes to the Benchmark could impact this transaction.
Confidentiality: No part of this material may, without GSAM's prior written consent, be (i) copied, photocopied or duplicated in any form, by any means, or (ii) distributed to any person that is not an employee, officer, director, or authorized agent of the recipient.
GSAM Services Private Limited (formerly Goldman Sachs Asset Management (India) Private Limited) acts as the Investment Advisor, providing non-binding non-discretionary investment advice to dedicated offshore mandates, involving Indian and overseas securities, managed by GSAM entities based outside India. Members of the India team do not participate in the investment decision making process.